You can refer to the article how to use interfaces in go (based on russ cox’s description of interfaces): The source of the confusion is that in most languages, if you have an interface type that defines a set of methods, the class that. I wanted to do a generic comparison between an interface and an abstract class on the basis of their usage.
How Do The Various Layers Of Cyberspace Impact Cybersecurity Policy
The @interface keyword is used to declare a new annotation type.
But implemented by a single class then how the compiler will identify the which method is for which interface?
Qual a diferença entre classe e interface e em que momento devo usar uma ou outra? Two interfaces with same method names and signatures. When would one want to use an interface. It is a set of methods, but.
An interface promises nothing about an action! On the other hand, implementing an interface just says it need to behave that way but the. An interface is a contract: An interface is two things:
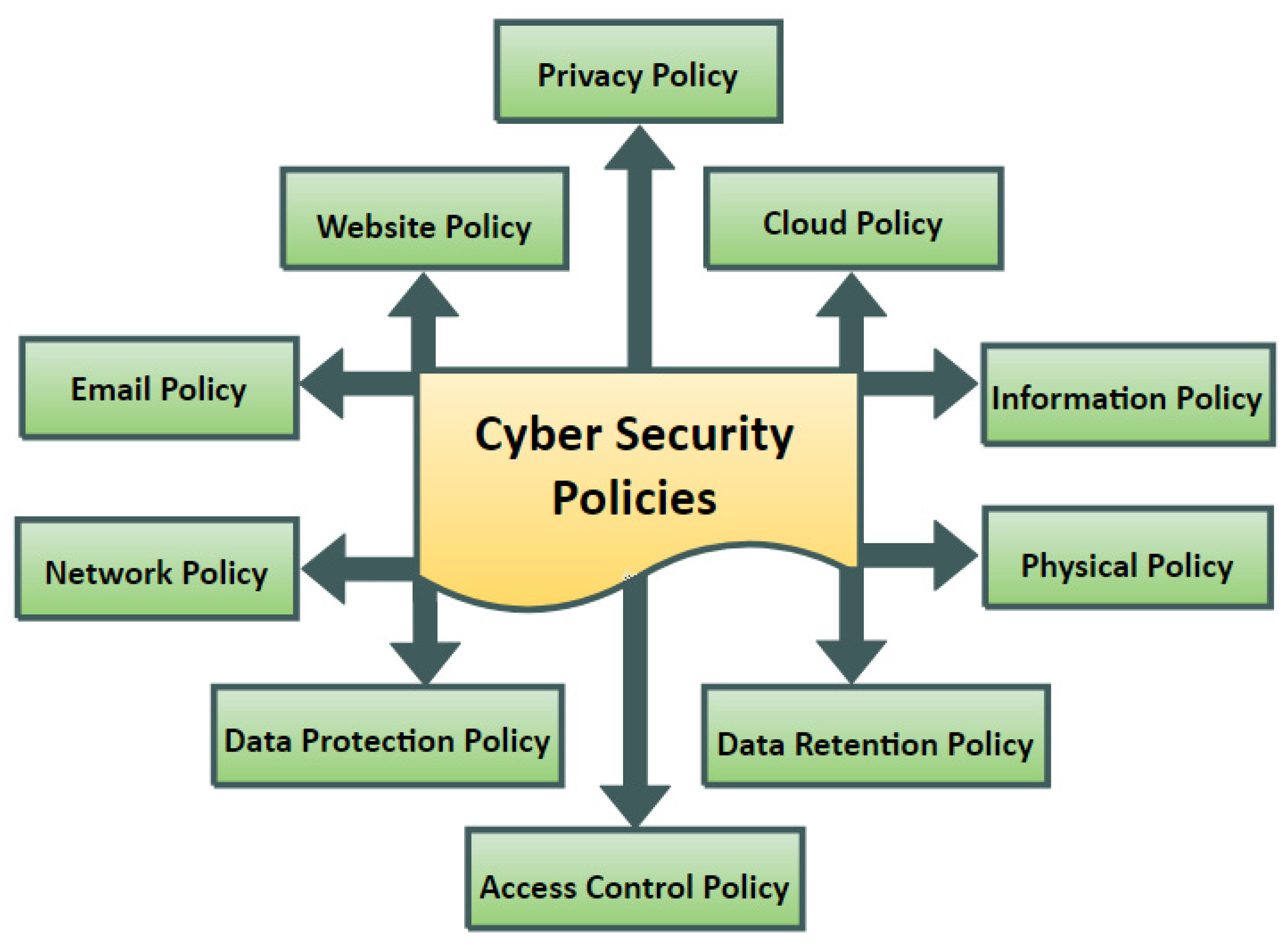
This may be a generic oop question.
Hi, interface and type, looks similar but interfaces can use for declaration merging and extends and implements which type cannot do. A good example of when exactly to use interfaces specifically in java would be ideal and any specific rulings that apply.








